Why Choose Our Network Solutions
Zero IT’s network solutions deliver reliable, scalable, and secure connectivity tailored to your business needs. Benefit from high-performance infrastructure, enhanced security, and minimized downtime, ensuring your operations run smoothly and efficiently in both on-premises and cloud environments.
Firewall Baseline Security
Even the best internal I.T. teams don’t always have the bandwidth to review firewalls for security gaps, audits, and compliance. The result? Many businesses end up with outdated or misconfigured firewalls that attackers love. Ask yourself:
- Patched & hardened — up to date against threats
- Advanced features on — filtering, inspection, reporting
- Secure remote access — modern VPN with user awareness
A firewall alone isn’t security. Without proper setup, monitoring, and employee awareness, it’s just expensive hardware. We make sure your firewall works as a shield — not a doorstop.
Wireless Reliability
Slow, unreliable Wi-Fi is costing you money. Employees waste time reconnecting, customers get frustrated with poor service, and weak coverage leaves gaps that attackers can exploit. Outdated Wi-Fi setups drag down productivity and keep your business stuck in the past.
- Fast & reliable — coverage where you need it
- Secure by design — encrypted & segmented
- Future-ready — Wi-Fi 6/7, built to scale
Because Wi-Fi should power productivity — not waste time or hold you back.
Network Infrastructure
Your network is the backbone of your business. Outdated switches, messy cabling, and “rogue” devices lead to downtime, bottlenecks, and security gaps. Unsegmented IoT devices only make the problem worse, leaving your business exposed. We help small businesses:
- Improve performance with modern hardware & cabling
- Eliminate weak links — rogue switches & IoT segmentation
- Simplify management so your team can stay focused
Don’t let legacy gear or sloppy infrastructure drag down productivity or weaken your security posture — upgrade before it costs you.
Network Segmentation: A Smarter, More Secure Network
Modern networks are more than just cables and switches—they are the foundation of your business operations. Proper network segmentation ensures that devices and users are grouped into dedicated VLANs (Virtual Local Area Networks) based on function and trust level.
By isolating critical systems (servers, production PCs, VoIP phones) from high-risk devices such as guest laptops, mobile devices, and IoT equipment, segmentation reduces the attack surface and limits lateral movement of threats. If a guest or IoT device is compromised, it cannot easily spread malware into your production or server environment.
Network Segmentation: A Smarter, More Secure Network
Modern networks are more than just cables and switches—they are the foundation of your business operations. Proper network segmentation ensures that devices and users are grouped into dedicated VLANs (Virtual Local Area Networks) based on function and trust level.
By isolating critical systems (servers, production PCs, VoIP phones) from high-risk devices such as guest laptops, mobile devices, and IoT equipment, segmentation reduces the attack surface and limits lateral movement of threats. If a guest or IoT device is compromised, it cannot easily spread malware into your production or server environment.
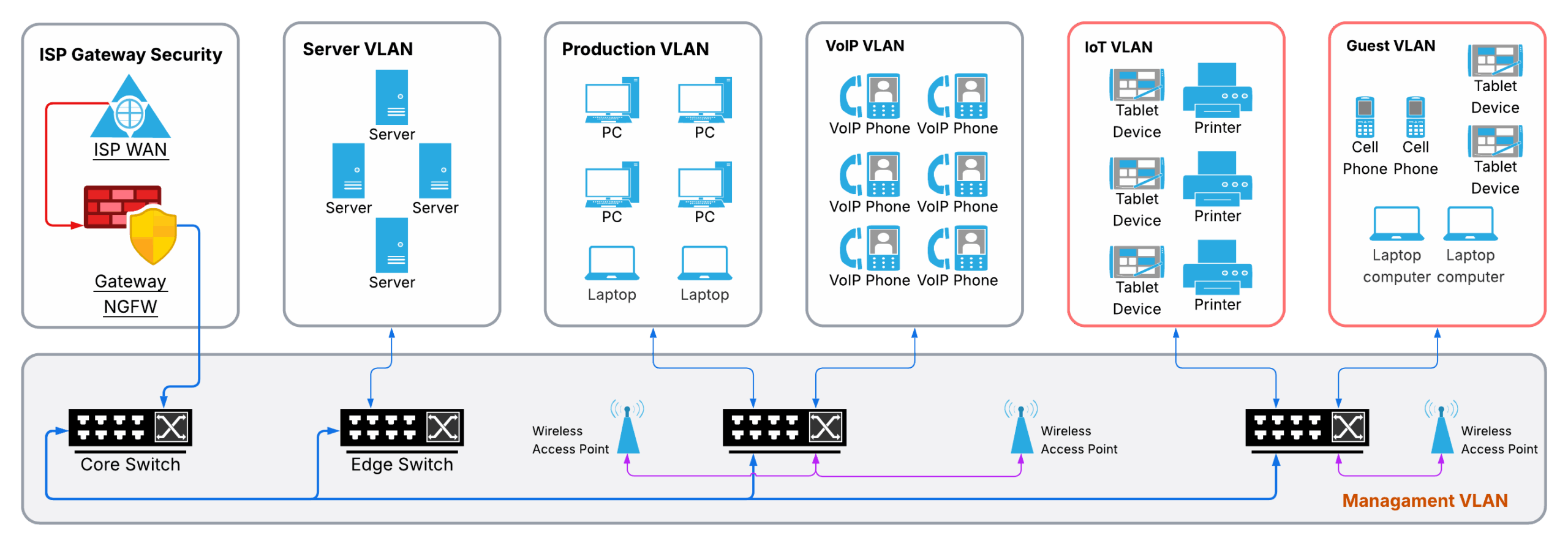
Why Segmentation is Important
Security First – Guest and IoT devices are common targets for attackers. Segmentation ensures they live in their own isolated zones, preventing access to sensitive business systems.
Quality of Service (QoS) – With traffic separated, business-critical applications like VoIP or ERP systems can be prioritized for bandwidth and reliability without interference from streaming, guest usage, or background IoT chatter.
Regulatory Compliance – Many standards (HIPAA, PCI-DSS, NIST/CMMC) require controlled access to sensitive data. Segmentation helps meet these requirements.
Operational Efficiency – Faster troubleshooting, better visibility, and more predictable performance across the network.
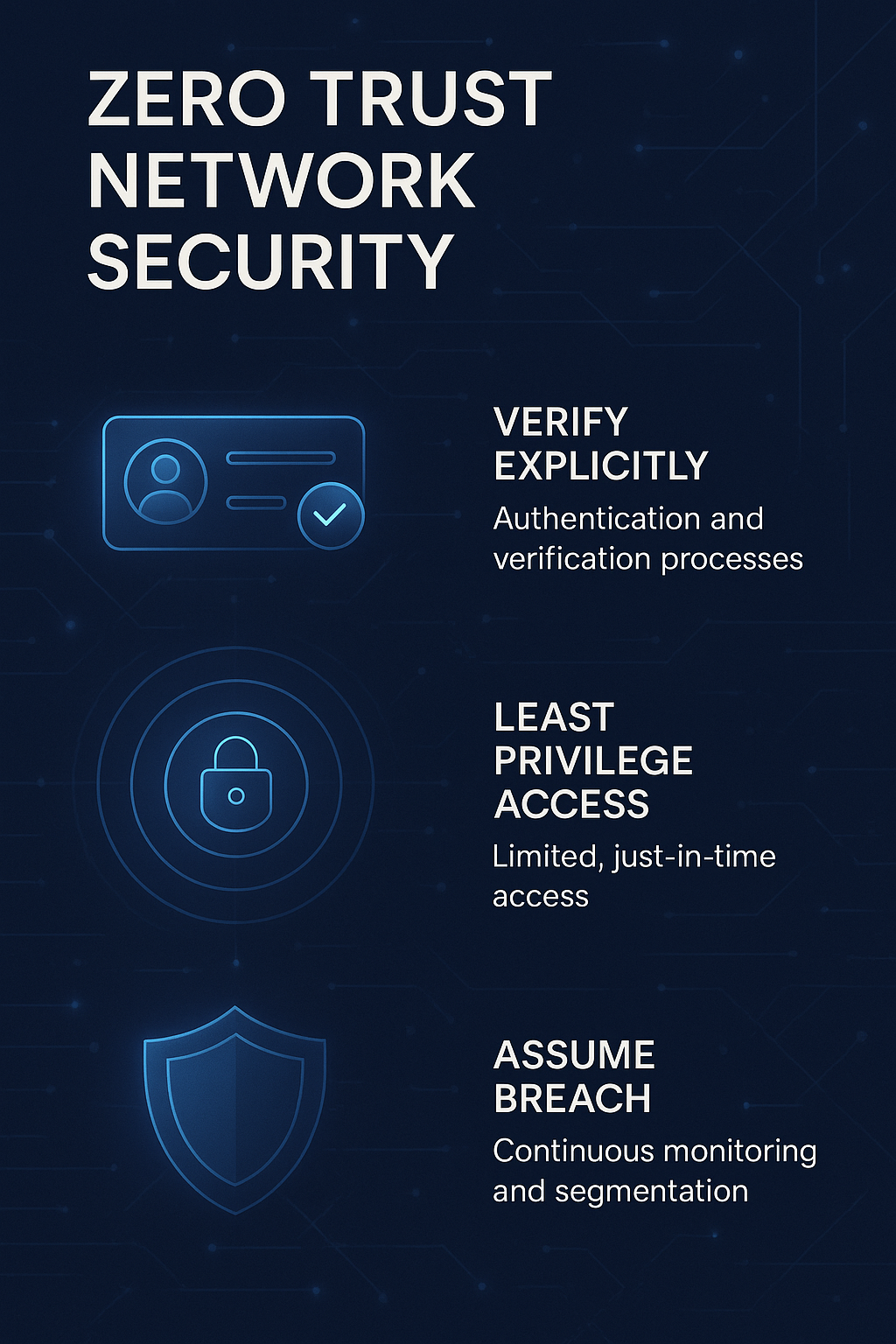
Zero Trust Framework
Zero Trust isn’t just about identity and access control; it’s also about not trusting anything by default, even inside your network. Segmentation directly supports that philosophy:
Least Privilege Access – Each VLAN (servers, production, VoIP, IoT, guests) is restricted to what it needs, nothing more.
Isolation by Default – Guest and IoT networks cannot freely talk to production or server VLANs. All access is explicitly allowed through policy.
Policy Enforcement at the Edge – Your NGFW between VLANs ensures that only authorized traffic flows, which is a Zero Trust principle.
Containment – If one device is compromised, segmentation prevents it from moving laterally into more critical parts of the network.
So while segmentation alone isn’t the entire Zero Trust architecture, it’s one of the core building blocks.
Take Control of Your Network Security
Modern businesses can’t afford to leave their networks unprotected. With Zero Trust principles and proper segmentation, you gain stronger security, better performance, and peace of mind.
Ready to secure your network?
Contact us today to schedule a consultation and see how we can design a safer, smarter network tailored to your business.
Get in Touch
Contact Zero IT LLC
Reach out to our team for expert IT solutions and support. We are here to assist you with your technology needs.
Email Us
Send us an email at contact@zeroit.llc for inquiries or support. Our team responds promptly to your messages.
Call Us
Call our office at +1 (602) 902-0340 for immediate assistance or to schedule a consultation.
